About Livy
Welcome to Livy Documentation, find developer guides, code examples, API references, and more.
Livy is a verifiable computation platform using trusted execution environments. Livy compiles your applications written in any language into a deterministic build to ensure reproducibility and verifiability. When this build runs inside an Intel TDX enclave, Livy generates attestations capturing the enclave’s identity, runtime integrity, and hashes binding together the binary, input, and output.
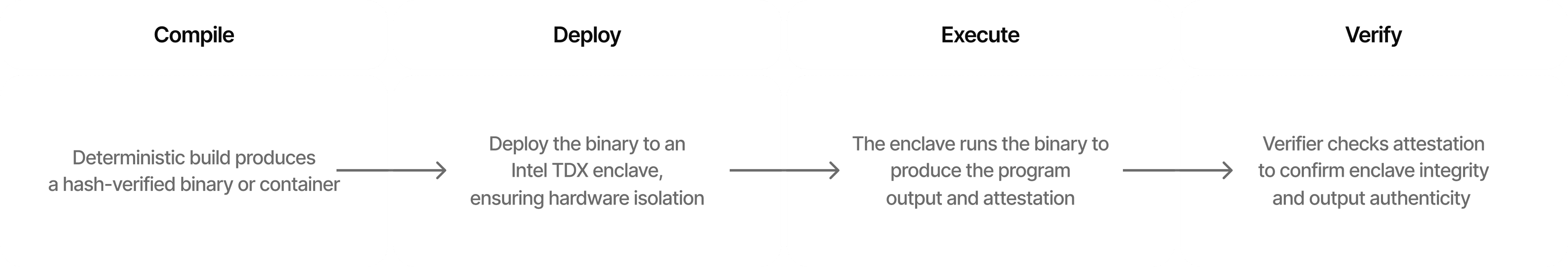
How it works
Livy provides verifiable compute infrastructure using Intel TDX (Trusted Execution Environments). Developers deploy applications in any language—Rust, Go, JavaScript—through our automated pipeline. The code compiles inside a secure TEE enclave, creating a deterministic build that ensures reproducibility.
When the application executes with input data, the TEE generates cryptographic attestations that capture three critical elements: the exact binary hash (proving what code ran), the input data (proving what information was processed), and the output results (proving what was produced). This attestation is cryptographically signed by the Intel hardware, creating an unbreakable chain of custody.
Every execution produces an individual attestation that anyone can verify independently. The verification is open-source—users don't need to trust Livy or the application developer. They can cryptographically verify that specific code processed specific data to produce specific outputs, all within a secure hardware environment. This creates complete data provenance: an auditable trail from data source through computation to final result.