Attestations
Attestation is a security process that verifies the identity and integrity of a computing environment, especially within a Trusted Execution Environment (TEE). Remote attestation specifically enables a trusted component (the attester) to prove to a remote challenger that it is executing computations inside a secure and protected domain. The challenger then confirms this trust by validating cryptographic signatures and comparing collected measurements against known, trusted reference values
On a TDX-enabled machine, the attester runs inside a Trust Domain (TD) and handles remote attestation requests. When a challenger sends a request, the attester generates a TD quote proving the TD is properly instantiated. This quote, produced by the TDX module and signed by the Quoting Enclave, contains measurements of the TDX Trusted Computing Base (TCB) and the software loaded into the TD. The quote also includes a certificate chain anchored by a certificate issued by Intel.

Figure 1: Certificate Chain
The challenger verifies the authenticity of the TD quote to confirm that the attester runs on a genuine TDX-enabled platform with expected software measurements. If verified, the challenger can establish a secure channel or release secrets to the attester.
Remote Attestation
Attestation of a TD consists of first generating a local attestation report, then extending it with digital signatures and certificates to enable remote verification off the platform. The host TDX platform thus enables remote attestation.
Workflow
The process involves several steps: First, measuring the loaded software during build time and runtime of the Trust Domain. Then, retrieving the TD measurements along with platform TCB information. Finally, deriving a quote from the TD report (as mentioned in a prior blog post). A third party can then use this quote to verify whether the TD runs on a genuine TDX platform with the expected TCB versions and software measurements.
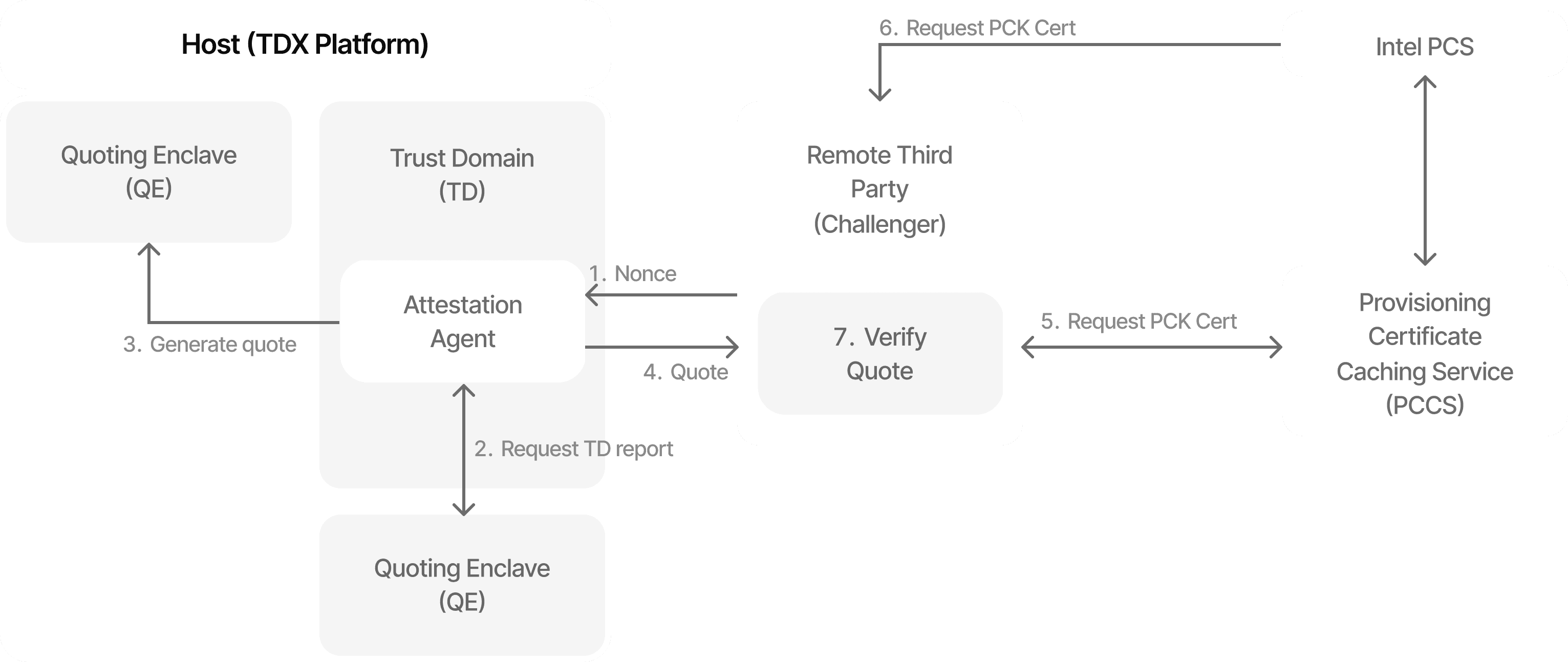
Figure 2: Remote Attestation Flow
Measurements
TDX provides two types of measurement registers for each Trusted Domain: a build-time measurement register called Measurement of Trust Domain (MRTD) and Runtime Measurement Registers (RTMRs). These measurement registers correspond to TPM PCRs.

Figure 3: Mapping of TDX measurements Register and TPM PCRs
Generating a TD Report
A TD report is generated within a TD under the TDX Module’s functionality. It uses an initialized report structure and some user-provided report data called REPORTDATA, a 64-byte field that Livy leverages to build a provenance layer on top.
The TDX Module calls a CPU instruction with the TD’s measurements and custom data to generate the TD report, which the CPU protects using a CPU-only HMAC key. This report is returned to the TD for local verification. The report can be verified only on the platform and not off-platform.
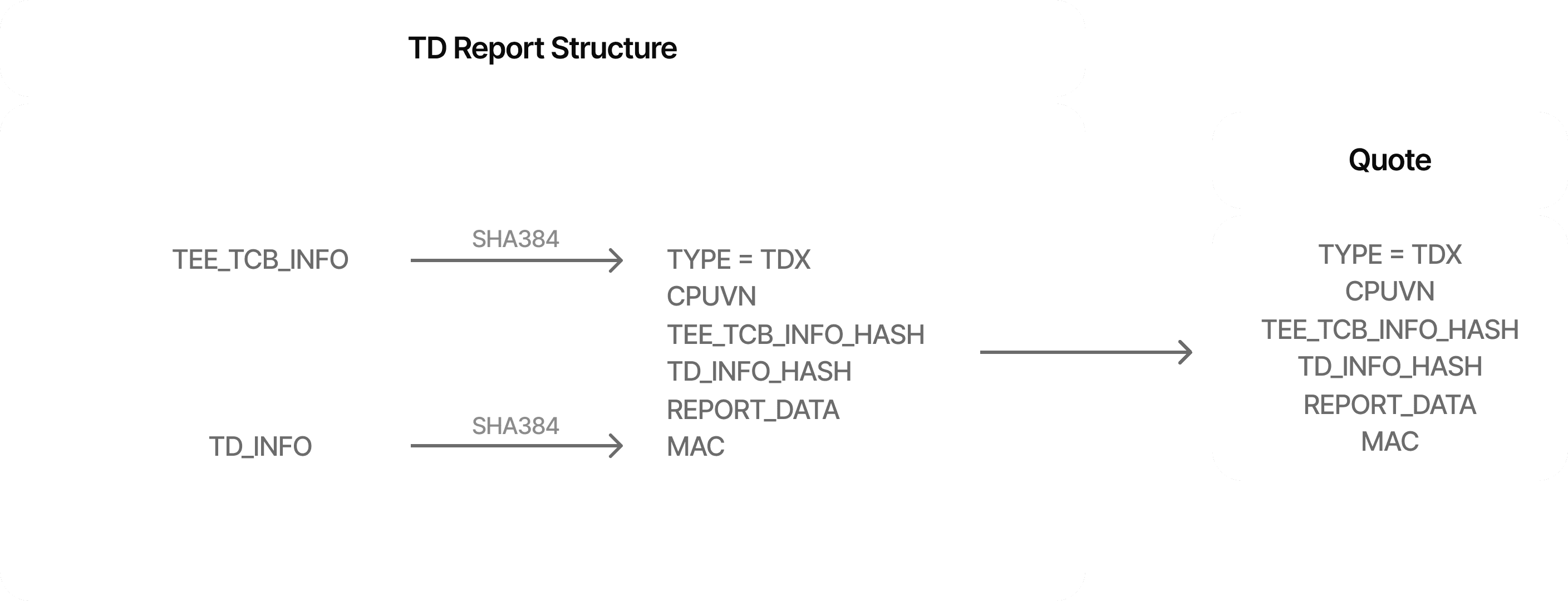
Figure 4: TD Report Structure
Deriving the Quote
To allow third-party verification off the platform, the TD report must be converted into a quote. TDX reuses the remote attestation mechanism from SGX for this purpose. The TD requests the Quoting Enclave (QE) on the host platform to sign the TD report, producing a remotely verifiable quote. The QE uses the EVERIFYREPORT2 instruction to verify the TD report’s HMAC. If successful, the QE signs the TD report using its certified attestation key to generate the quote. This operation replaces the MAC integrity protection of the TD report with digital signature protection, enabling any party to verify the provenance and integrity of the quote using public key certificates.
Remote Attestation
Platform setup for Remote Attestation
Configuring the attestation infra involves registering with the Intel PCS( Intel Platform Certificate Services).